Being in the security business, we must expect that there will be attempts to circumvent and cheat the system. That is a given, and we must be prepared for all such eventualities.
No one can ever guarantee that a system is totally immune to all forms of attack. Nothing in this world is certain accept the fact that people will try and cheat if there is any money to be made.
TeMWIA is only too aware of such risks and has thus brought together world experts from all relevant fields to ensure that the system we develop is as secure as possible and lives up to the medical dictum expressed as 'do no harm'. The system can never be subverted to declare a forged item as genuine.
We will always ensure that our system is as safe from external disruption as possible. However, we will never assume the data in the system is 'clean'.
The integrity of every data record is cryptographically checked every time it is accessed. If there is a problem, the system will always fail 'safe' - it will not mislead people into a false sense of security.
If a product's details have been tampered with in any way, it will be immediately detected and reported to the system administrators. A user who checks a code and it shows a cryptographic error, will be told that the item needs further investigation and will be prompted to leave their details with a promise to provide prompt feedback.
Let us look at a few examples of what would happen if some form of forgery or attack is attempted.
A: We try our best to ensure the safety of our web site but our data security does not depend on that. We acknowledge that even the most 'secure' sites have been compromised so we must be prepared for the worst.
Our security does not depend on the integrity of the site but rather on the integrity of the data.
Using advanced cryptographic methods we can guarantee that no one can add false data to our web site or alter existing data. An attack on the site can temporarily take it down (stop it working) but cannot surreptitiously add products and present them as genuine. Guaranteed.
A: If he uses the labels on goods that are not identical to the original, then obviously the forgery will be worthless as the description on the web will no longer match the actual product so the very first scan will show it up as an obvious forgery.
If the forgery is an exact duplicate product with identical packaging (including identical batch numbers and so on) that too will not work for the forger:
When a QR code is scanned, the purchaser is asked to confirm whether he has purchased the item or not. Once confirmed as sold, any attempt to scan an identical code will come up with an 'already sold' message putting the purchaser on his guard.
This leaves the forger with a massive loss rather than a healthy profit, as he will never have the opportunity to sell his wares in any significant numbers beyond, maybe, the first few. This is the primary aim of the TeMWIA system. To detect and report forgeries extremely quickly and thereby make it totally uneconomical to forge products protected by the TeMWIA system.
It is worth pointing out that the system is applicable equally to bulk movements. All along the supply chain, bulk cases can be checked and forgeries stopped even before they reach the retail shelves.
Note the speed with which a forgery will be caught, compared to conventional methods, where a forgery may go undetected for a very long time – if it is detected at all.
That alone is enough to stop a potential forger from trying his hand with products protected by security labels.
TeMWIA can also apply intelligent rules and heuristic data analysis to detect forgeries. For example, for products sold only in specific countries, TeMWIA can identify scans originating from irregular locations and provide appropriate warnings.
The same analysis can be used to detect 'grey market' trading in countries not authorized to distribute the goods in question.
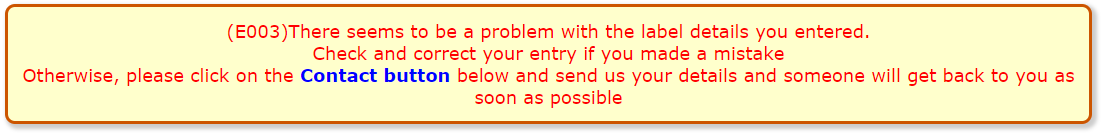
A: This will obviously be caught at the very first attempt as there would not be any matching items recorded on the web site. The following message would be displayed:
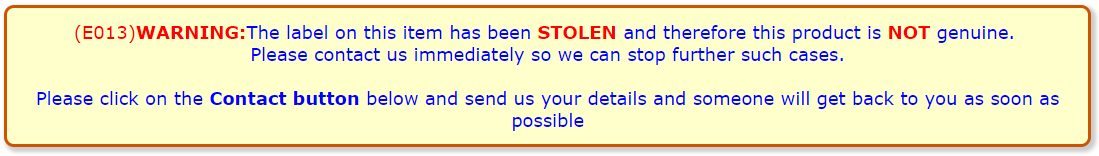
If theft of the labels is known, the stolen number range will be recorded on the system as "stolen", and described on the web site as such.